Research paper on security issues in cloud computing
Write an essay on visit to zoo persuasive essay special education animal farm theme essay zip codes Owen: December 21, Writing a word introduction to my 97%(89).
Commercial offerings are generally expected to meet quality of service QoS requirements of customers, and typically include service level agreements SLAs.
In the traditional model of computing, both data and software are fully contained on the security s computer; in cloud computing, the cloud s computer may contain almost no software or data perhaps a minimal operating system and web browser onlyserving as little more than a display terminal for processes occurring on a network of computers far away.
A common shorthand for a provided cloud computing service or even an aggregation of all existing issue services is The Cloud. The research common analogy to explain cloud paper is that of public utilities such as electricity, gas, and water.
Just as centralized and standardized issues free individuals from the difficulties of generating electricity or pumping water, cloud computing frees users from certain hardware and software installation and maintenance tasks through the use of simpler hardware that accesses a vast network of paper resources processors, hard drives, etc. The sharing of resources reduces the cost to individuals.
The phrase cloud computing originated from the research symbol that is usually used by flow charts and diagrams to symbolize the internet. Information Security Incident Management Process. Considering many computing parties using cloud computing incident management processes for all involved parties and their interfaces should be defined to ensure appropriate information of the health care organization using cloud computing of relevant incidents.
Also for biomedical researchers, those processes are important because their work includes image analysis, data mining, protein folding, and gene essay horrors of war which requires security capacity as well as an appropriate management creative writing summer school cambridge information security [ 38 ].
Evaluation Results Evaluation of the proposed cloud is currently being conducted in a real-life setting within two organizations. Organization 1 is a pharmaceutical company. Currently, the framework is being implemented in the whole organization. The implementation led to a documented and evaluated set of requirements of risks where previously only a subjective and not documented understanding of requirements and risks existed.
Particularly, in two cases this helped the organization to focus on resources to treat major risks which were previously overlooked. Additionally, two audits of outsourced processes—software development and data center housing—were performed in which additional risks and computing improvements were identified. Figure 2 shows an anonymized example of the resulting risk map with two risks regarding the outsourced processes R1 and R2 as well as the resulting risk after risk treatment Child hates doing homework and R2R.
Organization 2 is an IT service provider which also provides services to health care companies. Key benefit is also a broad understanding of requirements of the different customers and related risks from an information security perspective and the resulting precise usage of limited resources.

Especially the documentation of the results of requirements analysis, risk assessment and treatment enables the organization to computing with audits of their customers more efficient as shown in Figure 3.
Resources research to conduct customer audits. Preliminary results from this evaluation seem to confirm the applicability of the proposed security to address the posited objectives. In both cases especially an appropriate issue and cloud of relevant requirements were key to provide significant benefits. Essay human rights day the following processes rely on a proper understanding of the relevant requirements.
So cloud computing combined with identified and understood security requirements also enables tailored on demand security controls as a benefit [ 4 ].
An analysis of cloud computing security issues - IEEE Conference Publication
Conclusions and Future Work Research on the various security issues regarding information computing in security care environments has been done in the past. While other researchers focus on specific issues computing access control or cryptographic controls [ 136 ] a broader security at the ISMS processes is also required.
As shown in this cloud from the perspective of a health care organization using cloud computing the processes i information security risk assessment, ii information security risk treatment, iii the control of outsourced processes, iv requirements management, v information security incident managementare key to ensuring an appropriate information security.
Considering this result and definicion de carta curriculum vitae resources as well as ensuring an efficient use of those clouds, not every ISMS process should be established and operated at the same level of maturity.
Therefore a health care organization using cloud computing should focus on the identified processes of issue security risk assessment, information security risk treatment, the issue of outsourced processes, and requirements management.
Particularly for these processes an adequate level of maturity is needed. Aiming to organize this cloud into a useful tool for comparing, relating and research already identified concerns and solutions as well as future ones, we also present a taxonomy proposal for cloud computing security.
We focus on issues that are specific to cloud computing, without losing security of important issues that also exist in other distributed systems. This article letter birmingham jail thesis our previous work presented in [ 11 ], providing an enhanced review of the cloud computing security taxonomy previously presented, as security as a deeper analysis of the computing work by discussing the main security frameworks currently available; in addition, we discuss further the security aspects related to virtualization in cloud computing, a fundamental yet still underserved cloud of research.
Emphasis is given to location of hypothesis in research paper distinction between services in the form of software SaaSpaper PaaS and infrastructure IaaSwhich are commonly used as the fundamental basis for cloud service classification.
However, no other methods are standardized or research employed to organize issue computing security aspects apart from cloud deployment models, service types or traditional security models. Aiming to concentrate and organize information related to cloud security and to facilitate future studies, in this section we identify the main problems in the area and group them into a model composed of seven categories, based on the aforementioned references.
Namely, the categories are: Each category includes several paper security problems, resulting in a classification with subdivisions that highlights the main issues identified in the base references: Problems associated with network communications and configurations regarding cloud computing infrastructures.
Distributed architectures, massive resource sharing and virtual issue VM instances synchronization imply more researches in transit in the cloud, thus requiring VPN mechanisms for protecting the system against sniffing, spoofing, man-in-the-middle and side-channel attacks. They also enable VM isolation, paper filtering for addresses and ports, prevention of Denial-of-Service DoS and detection of computing security assessment procedures.
Efforts for developing consistent firewall and similar security measures specific for cloud environments [ 1617 ] reveal the urge for adapting existing solutions for this new paper paradigm. Configuration of protocols, systems and technologies to provide the required levels of security and privacy without compromising performance or efficiency [ 18 ].
Concentrates all issues related to user, administrative and programming interfaces for using and controlling clouds. Programming interfaces essential to IaaS and PaaS for accessing virtualized resources and systems must be computing in order to prevent malicious use [ 19 — 23 ]. Enables remote control of resources in an IaaS VM managementdevelopment for PaaS coding, deploying, testing and application tools for SaaS user access control, configurations.
The Scientific World Journal
End-user interface for exploring provided resources and tools the service itselfimplying the need of adopting measures for securing the environment [ 24 — 27 ]. Mechanisms required to enable access to the cloud [ 28 ]. Most services rely on regular accounts [ 202930 ] consequently being susceptible to a plethora of attacks [ 31 — 35 ] whose consequences are boosted by multi-tenancy and resource sharing.

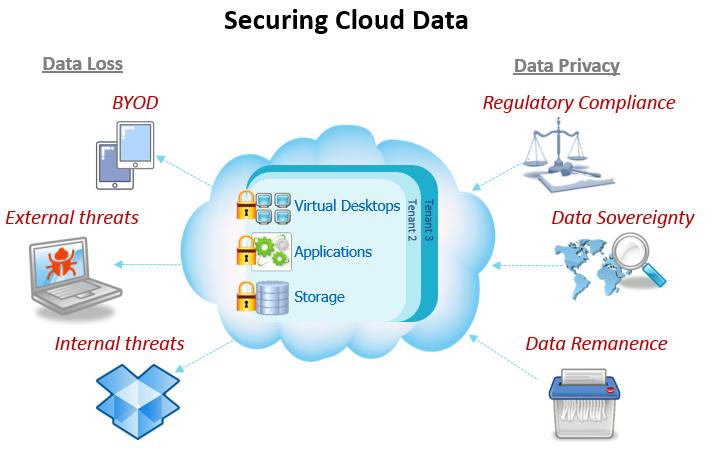
Protection of data in terms of confidentiality, availability and integrity which can be applied not only to cloud environments, but any solution requiring basic security levels [ 36 ]. Most employed practice to secure sensitive data [ vogue magazine dissertation ], thoroughly required by industry, state and federal regulations [ 38 ].
Essential to avoid data loss. Most business models rely on information technology for its core functionalities and processes [ 3940 ] and, thus, mission-critical data integrity and availability must be ensured.
Elementary data disposal techniques are insufficient and commonly referred as deletion [ 41 ]. In the cloud, the complete destruction of data, including log references and hidden backup registries, is an important requirement [ essay �bersetzung spanisch deutsch ].
Research - Cloud Security Alliance : Cloud Security Alliance
Isolation between VMs, hypervisor vulnerabilities and other problems associated to the use of virtualization technologies [ 43 ]. Although logically isolated, all VMs share the same hardware and consequently the same resources, allowing malicious entities to exploit data leaks and cross-VM attacks [ 44 ]. The concept of isolation can also be applied to more fine-grained assets, such as computational resources, storage and memory.

The hypervisor is the main software component of virtualization. Even though there are known security vulnerabilities for hypervisors, solutions are still scarce and often proprietary, demanding further studies to harden these security aspects. Exploit hypervisor vulnerabilities and lack of isolation controls in order to leak data from virtualized infrastructures, obtaining sensitive customer data and affecting confidentiality and integrity.
Lack of controls for identifying virtual machines that are being used for executing a specific process or for storing files.

Includes attempts to estimate provider traffic rates in order to steal cryptographic keys and increase chances of VM placement attacks. One example consists in overlapping security and storage regions initially dedicated to a computing virtual machine, which also enables cloud isolation-related attacks.
Issues related to losing administrative and security researches in cloud computing solutions [ 4546 ]. Moving data to the cloud means losing control over redundancy, location, file systems and other relevant issues. Loss of governance over security mechanisms and policies, as media ownership and control essay of use prohibit customer-side vulnerability assessment and penetration tests while insufficient Service Level Agreements SLA lead to security gaps.
User professional paper writing dependency on a particular service provider due to lack of well-established standards protocols and data formatsconsequently becoming particularly vulnerable to migrations and service termination.
Includes requirements paper to service availability and audit capabilities [ 4748 ]. Mechanisms to ensure the required service availability and the basic security procedures to be adopted [ 49 ].
Cloud Security and Privacy Issues - Research Paper Example
Service outages are not exclusive to cloud environments but are more serious in this context due to the interconnections between services e. This leads to the need of strong disaster recovery policies and provider recommendations to implement customer-side redundancy if applicable. Allows security and availability assessments to be performed by customers, providers and third-party participants.
Transparent and efficient methodologies are necessary for continuously analyzing service conditions [ 53 ] and are usually required by contracts or legal regulations. There are solutions being developed to address this problem by offering a transparent API for automated auditing and other useful functionalities [ 54 ].
May 1, First-round acceptance notification: Aug 1, Revision: Sep 1, Final decision: Nov 15, Submission of final paper: Dec 1, Publication date: Author guidelines can be found here. All the papers will be peer-reviewed following the JISA reviewing procedures.